Exploring the Potential Dangers and Consequences of Data Breaches in t…
페이지 정보

본문
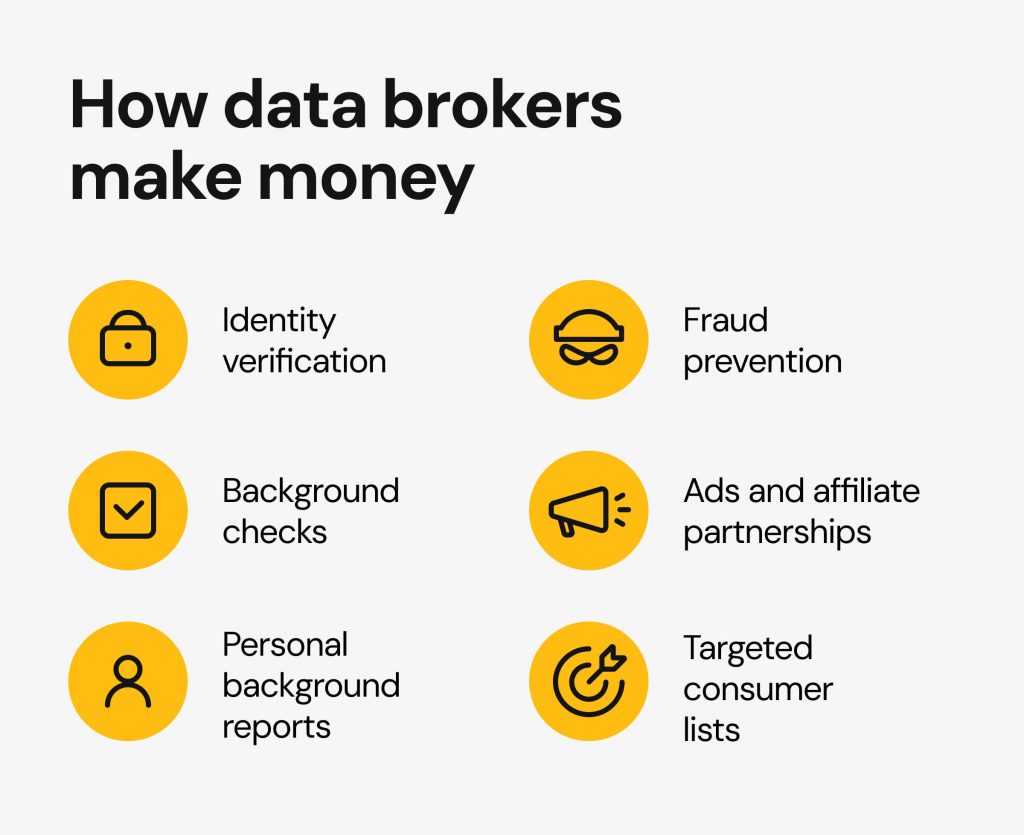
In a world where personal information flows freely, numerous challenges arise. These challenges impact both individuals and organizations. Privacy is often compromised, leaving people exposed. With every transaction, sensitive details risk falling into the wrong hands. It’s a precarious situation, yet many remain unaware of the potential consequences.
Companies that specialize in gathering and selling personal profiles operate in a gray area. They collect vast amounts of information through various means, then package and sell it. This practice raises profound ethical questions about consent and ownership. Additionally, the increasing sophistication of cyber threats intensifies concerns for unsuspecting consumers. Vulnerabilities can lead to serious repercussions.
As technology evolves, so do the tactics of those attempting to exploit weaknesses. Security measures may falter, revealing significant gaps. When such events occur, trust erodes and opt out radaris reputations suffer. This dynamic creates a cycle of fear and uncertainty. Moreover, victims of these incidents often face long-term challenges, both financially and emotionally.
Understanding the landscape of information reselling is essential. Consumers must remain vigilant and informed about who holds their data and how it is used. Awareness fosters proactive behavior, empowering individuals to take charge of their privacy. Those in positions of authority must also prioritize implementing stricter regulations and safeguards. In doing so, they can mitigate potential fallout from unforeseen exposures.
Understanding Data Brokers and Their Role

In today’s interconnected world, vast amounts of information circulate daily. Companies and individuals alike rely on this information for various purposes. But who collects and sells this data? This is where entities known for aggregating public and private information come into play. They operate in a complex ecosystem, influencing marketing, credit assessments, and even personal security.
Entities specializing in gathering information aggregate details from multiple sources. This can include public records, social media profiles, and online behaviors. Their purpose is to create comprehensive profiles of individuals. Such profiles are valuable for businesses seeking to target specific demographics. They analyze patterns and trends derived from this information. However, the methods of collection often raise ethical questions.
By compiling extensive databases, these entities serve various clients. Businesses utilize their services to enhance marketing strategies, tailor advertisements, and improve customer engagement. They help companies identify potential customers, predict buying habits, and even assess creditworthiness. Yet, while providing these services, they often operate in shadows, leaving consumers unaware of how their information is being used.
In an era where privacy is paramount, the role of these aggregators remains contentious. While they facilitate beneficial services, their practices can infringe on individual privacy. Moreover, misuse of this information can lead to negative outcomes. With a powerful collection of personal details, the potential for exploitation becomes a significant concern. Balancing utility and privacy is a constant struggle.
Understanding this ecosystem is essential for navigating modern privacy challenges. Awareness fosters informed choices regarding sharing personal information. It’s crucial to recognize how these entities operate and their implications for individual autonomy. By shining a light on their workings, consumers can better protect their personal data.
As technology evolves, so too will the methods and tools used by these information aggregators. Keeping pace with advancements is vital for both consumers and businesses. Adapting to new challenges ensures that information sharing remains both ethical and secure, paving the way for a more transparent future.
Common Types of Data Breaches
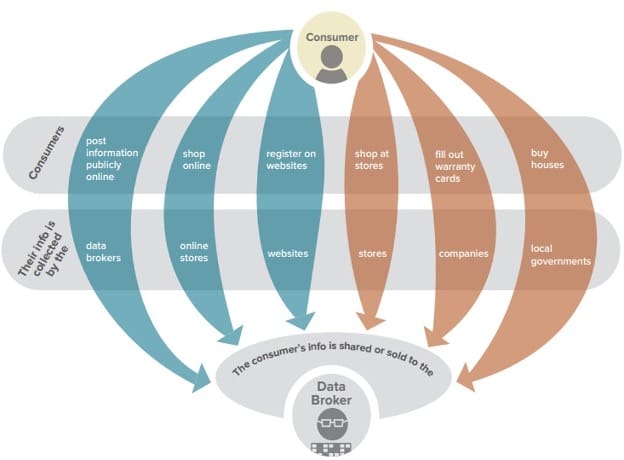
In today’s digital landscape, personal information is incredibly vulnerable. Every time an individual interacts online, they leave traces of their identity. Cybercriminals are constantly searching for opportunities to exploit this sensitive data. Understanding the common methods of exposure can empower individuals and organizations alike.
One prevalent method involves phishing attacks, where malicious actors impersonate trustworthy entities to steal information. Victims often receive emails or messages that appear legitimate. Clicking links or providing details can lead to significant compromises. Another tactic is malware infections. This software silently infiltrates systems, gathering sensitive information without user awareness.
In addition, physical theft of devices presents a serious challenge. Laptops, smartphones, and external drives can be lost or stolen, leading to unauthorized access. Moreover, cloud misconfigurations create vulnerabilities. When security settings are not properly managed, sensitive data can become publicly accessible, thereby exposing individuals and organizations to potential threats.
Moreover, insider threats can emerge from within, as employees may misuse access to sensitive information. This often happens due to negligence or malicious intent. Employees might inadvertently share information through unsecured channels. Consequently, organizations face significant challenges in safeguarding their data.
| Type of Breach | Description |
|---|---|
| Phishing | Fraudulent attempts to gain sensitive information through deception. |
| Malware | Software designed to disrupt, damage, or gain unauthorized access to systems. |
| Physical Theft | Loss of devices that contain personal or sensitive information. |
| Cloud Misconfiguration | Poorly managed security settings leading to exposure of sensitive data. |
| Insider Threats | Employees misuse their access to compromise sensitive information. |
In summary, awareness of these common methods of exposure is crucial. By recognizing how information can be compromised, individuals and organizations can better protect themselves from potential threats. As technology evolves, so do the tactics employed by cybercriminals. Therefore, vigilance and proactive measures remain essential for safeguarding personal and organizational information.
Impact on Consumer Privacy Rights
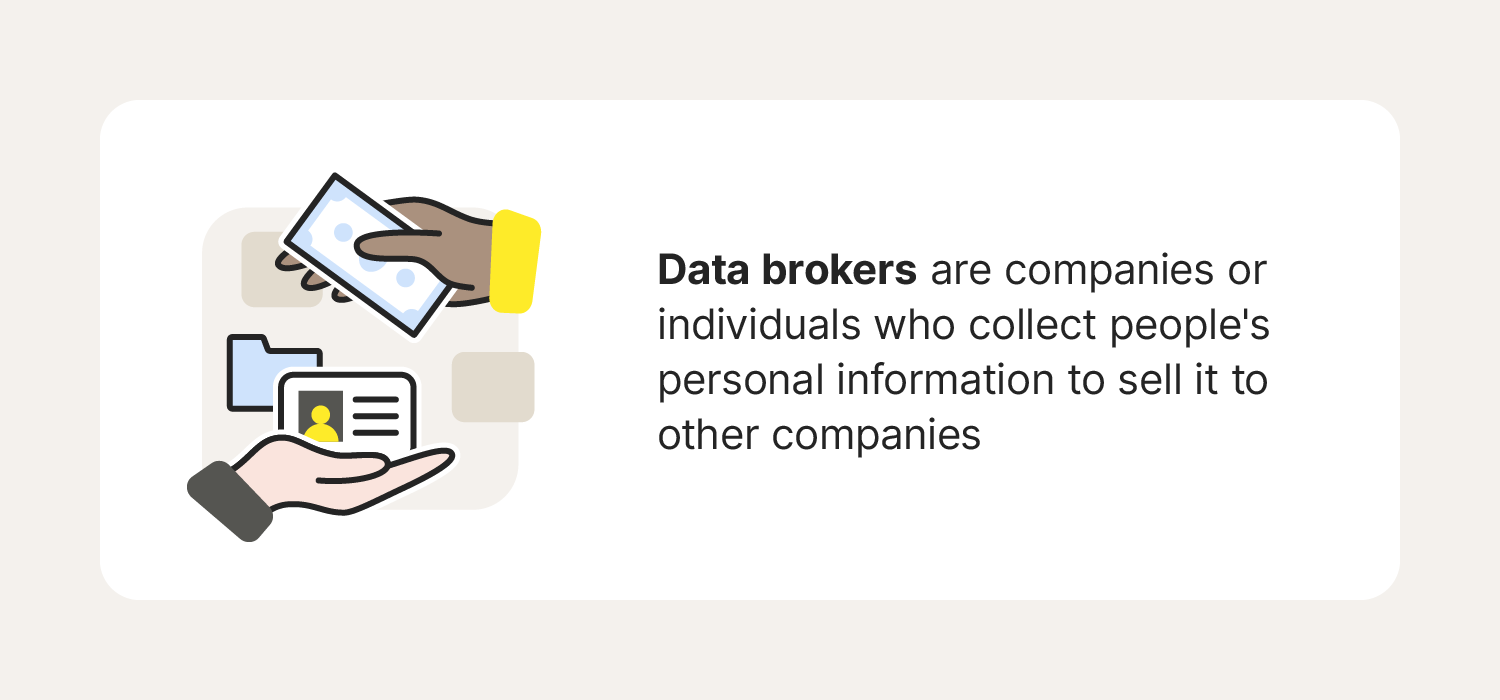
In today's digital landscape, individuals face numerous challenges regarding their personal information. The vast collection and sharing of personal details have reshaped the privacy experience. Many feel uncertain about who accesses their information and how it is utilized. This uncertainty has profound implications for consumer rights.
Every transaction, social media interaction, or online search contributes to a personal profile. These profiles can be aggregated, analyzed, and sold without consent. As a result, privacy has become a commodity. Unfortunately, this commodification often disregards individual autonomy over personal information.
Moreover, unauthorized access can lead to identity theft. Victims find themselves grappling with financial loss and emotional distress. The repercussions extend beyond immediate damage. They can erode trust in organizations that collect and manage sensitive data.
Additionally, the legal landscape surrounding privacy rights is evolving. Recent regulations aim to enhance transparency and accountability for companies. However, enforcement remains a significant challenge. Individuals often find navigating these complex frameworks overwhelming. This leads to a lack of awareness about their rights, ultimately leaving them vulnerable.
Consequently, the implications for consumer rights are far-reaching. When personal information is mishandled or exploited, individuals lose control over their identities. This not only affects personal security but also undermines public confidence in digital interactions.
As organizations adapt to these new regulations, maintaining consumer trust becomes crucial. Addressing privacy concerns proactively can foster a sense of security and respect for individuals. Ultimately, ensuring privacy rights is essential for a healthy relationship between consumers and organizations.
Consequences for Businesses and Individuals

In today's interconnected world, incidents involving sensitive information can have profound effects. Organizations and private citizens alike face potential fallout from exposure and misuse of personal details. Understanding these consequences is crucial for both parties. Increased scrutiny and loss of trust often follow such events. This creates a ripple effect that can extend far beyond immediate financial losses.
For businesses, repercussions can manifest in various forms. Legal actions, fines, and sanctions may arise if negligence is found. In severe cases, entire business operations may be jeopardized due to reputational damage. When customers lose faith in a brand, they often take their loyalty elsewhere. This loss isn't just financial; it can also mean diminished market presence and reduced competitive advantage.
Individuals, on their part, may experience identity theft, financial fraud, and a general sense of violation. Not only does privacy suffer, but ongoing anxiety about misuse of personal data can affect mental well-being. In extreme scenarios, victims find themselves tangled in legal battles to reclaim lost assets or identity. Trust in institutions dwindles, leading to a reluctance to engage with services that require personal information.
These ramifications create a complex landscape where both businesses and individuals must navigate carefully. While companies invest heavily in cybersecurity and compliance measures, individuals are compelled to adopt protective strategies. Awareness is key; understanding potential challenges can empower both groups. Restoring confidence takes time, effort, and a commitment to transparency. Ultimately, fostering a culture of accountability becomes essential in overcoming the negative impacts of sensitive information exposure.
Strategies for Mitigating Breach Risks
In today’s digital landscape, safeguarding sensitive information is paramount. Organizations and individuals alike face looming threats that can compromise personal and proprietary details. However, there are proactive steps that can be taken to enhance security and minimize vulnerability. Recognizing potential weaknesses is the first step towards establishing effective protections. By implementing robust security measures, it’s possible to create a safer environment for everyone involved.
Education is essential. Training employees about recognizing phishing attempts and social engineering techniques can significantly reduce human error. Regular workshops and seminars can keep staff informed about current threats. Furthermore, clear communication regarding security protocols can lead to a more vigilant workplace. When employees understand their role, they become a critical line of defense.
Another key aspect is technology. Utilizing advanced encryption methods can safeguard data during transmission and storage. A multi-layered approach that includes firewalls, antivirus software, and intrusion detection systems can deter unauthorized access. Regular updates and patch management should not be overlooked, as outdated software poses an open door to cybercriminals. Every small measure adds another layer of security, which collectively fortifies the organization.
Incident response plans also play a pivotal role. Establishing a clear plan ensures a swift reaction when a situation arises. Including specific roles and responsibilities can streamline communication during a crisis. Moreover, conducting periodic drills helps reinforce preparedness. When an organization is ready to act, the potential impact of an incident can be significantly reduced.
Lastly, collaboration is crucial. Sharing information about threats and vulnerabilities within networks fosters a culture of cybersecurity. Partnerships with industry peers can lead to shared insights and strategies. Engaging with cybersecurity firms can provide specialized knowledge and resources that may not be available internally. By working together, organizations can strengthen their defenses against potential attacks.
In conclusion, a multifaceted approach encompassing training, technology, planning, and collaboration is essential to combat ever-evolving security challenges. Such strategies not only protect individuals and organizations but also build a stronger framework for overall digital safety.
Strategies for Mitigating Breach Risks
In today’s interconnected landscape, securing sensitive information from unauthorized access is paramount. Effective measures must be implemented to protect personal and corporate assets. Organizations face continuous challenges, as threats evolve and become more sophisticated. Developing a proactive approach is essential for minimizing vulnerabilities.
Education of employees plays a critical role in safeguarding information. Regular training sessions can enhance awareness regarding potential threats. Staff members who understand phishing, social engineering, and other tactics are less likely to fall victim. Investing in such initiatives may seem minor, yet it can yield significant benefits.
Moreover, implementing robust security protocols is crucial. Utilizing encryption methods protects information from prying eyes. Firewalls and intrusion detection systems act as barriers against unauthorized attempts. Regular audits can help identify weaknesses in existing frameworks.
Collaboration with skilled cybersecurity professionals can also bolster defenses. External experts can conduct thorough assessments and simulations to pinpoint vulnerabilities. They bring specialized knowledge and tools to the table. Forming partnerships with these specialists ensures a more comprehensive security strategy.
Monitoring networks and systems is another vital component. Continuous surveillance allows for early detection of suspicious activity. Companies can respond quickly, mitigating potential fallout. Utilizing advanced analytics can uncover hidden patterns that suggest a looming threat.
Furthermore, establishing clear incident response plans is necessary. In the event of a compromise, having a structured process ensures swift action. Teams should practice these protocols regularly. This preparedness reduces confusion and enhances response efficiency.
Lastly, understanding regulatory requirements is essential. Compliance with various standards helps maintain consumer trust. Organizations should continuously adapt their approaches to meet evolving legal landscapes. Aligning practices with regulations not only protects assets but also fortifies reputations.
Ultimately, addressing vulnerabilities requires a multifaceted approach. By combining education, advanced security measures, and continual vigilance, entities can significantly improve their defensive posture. Each strategy contributes uniquely to the overall goal of safeguarding valuable information.
The Future of Data Security Measures
Emerging technologies and evolving challenges necessitate innovative approaches to safeguarding sensitive information. As society becomes increasingly reliant on digital platforms, the importance of robust protective strategies escalates. Various sectors are mobilizing to confront these challenges head-on. Continuous advancements in technology bring about new opportunities and threats alike.
Organizations must adopt a proactive mindset. Anticipating potential vulnerabilities is essential. Variables in the digital landscape change rapidly. Thus, adaptive security solutions become paramount.
- Artificial intelligence plays a pivotal role in monitoring activities.
- Machine learning algorithms can identify unusual patterns in real time.
- Encryption techniques are evolving to provide stronger safeguards.
- Decentralized technologies offer innovative methods for protecting user privacy.
Businesses also recognize that employee training is critical. Knowledgeable staff members can significantly reduce human errors that often lead to security lapses. By creating a culture of vigilance and accountability, organizations can boost their overall defenses. This collective effort fosters a resilient environment, where all stakeholders contribute to maintaining security.
Collaboration among entities is becoming increasingly significant. Sharing best practices and resources strengthens defenses across multiple sectors. Partnerships between private companies and government bodies can yield comprehensive strategies that benefit everyone involved. This united approach enhances overall preparedness against potential incidents.
- Investing in cutting-edge technologies is vital for future-proofing systems.
- Regular assessments and audits help in identifying areas for improvement.
- Establishing clear communication channels ensures a swift response during incidents.
Customer awareness also plays a crucial role in fostering a safe environment. As users become more informed about their rights and potential threats, they can make better decisions about their information. This empowerment creates a more proactive user base that demands higher standards from businesses. Eventually, this collective pressure can lead to substantial improvements across various sectors.
In conclusion, future security measures will hinge on a combination of advanced technology, collaborative efforts, ongoing education, and proactive user engagement. As new challenges arise, adaptability and resilience will define the landscape of information protection.
- 이전글менің сүйікті мамандығым эссе - менің мамандығым тәрбиеші эссе 24.09.25
- 다음글сіздің өміріңізге лайықты адамды қалай тартуға болады - қастандықтар 24.09.25
댓글목록
등록된 댓글이 없습니다.

